Protection matrix
From Erights
(Difference between revisions)
(Add a link to a real world example of this (basic) concept.) |
|||
| Line 6: | Line 6: | ||
and the context of each cell determines what operations on a particular object are permitted for a particular subject. | and the context of each cell determines what operations on a particular object are permitted for a particular subject. | ||
| - | == | + | == Artificial example == |
If: | If: | ||
| Line 19: | Line 19: | ||
It is not very usual to actually store permissions in the form of a 2-dimensional array as shown in the figure above but there are such systems which do so. Usually, the set of subjects and the set of objects are small and immutable. | It is not very usual to actually store permissions in the form of a 2-dimensional array as shown in the figure above but there are such systems which do so. Usually, the set of subjects and the set of objects are small and immutable. | ||
| + | |||
| + | == Real world examples == | ||
| + | |||
| + | * [[Protection matrixes in Minix]] | ||
Revision as of 15:39, 20 June 2009
Definition
One way how to capture the permissions of subjects to perform various operations with objects is to use a large matrix where:
- rows correspond to particular subjects
- columns correspond to particular objects
and the context of each cell determines what operations on a particular object are permitted for a particular subject.
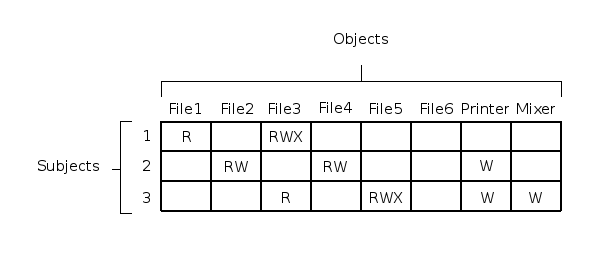
Artificial example
If:
- we have only three different subjects (1, 2 and 3)
- eight different objects (six files and a printer and a mixer)
- we recognize three different operations with objects (read, write and execute)
then one possible protection matrix may be:
The matrix determines which operations (R = read, W = write, X = execute) with particular objects are allowed for particular subjects.
It is not very usual to actually store permissions in the form of a 2-dimensional array as shown in the figure above but there are such systems which do so. Usually, the set of subjects and the set of objects are small and immutable.